The Secret Sauce of Cloud Desktop Security
July 26, 2018
When an organization considers moving their desktops to the cloud, data security becomes a primary concern. The prospect of relinquishing control of IT assets and possibly introducing risk to the business makes everyone pretty uncomfortable – to say the least. When it comes to virtual desktops in the cloud, the art is in balancing security and control on the one hand, with deployment speed, management simplicity, and cost containment on the other. At the end of the day, however, data security is paramount. When adopting cloud desktops, you essentially have two options, and there are trade-offs to consider:
Option A: DIY: Implement virtual desktops in the cloud on-your-own. You’ll have full control, but the deployment will take longer, be more difficult to maintain, and the related cloud compute costs can be wildly variable. Significantly, this option also comes with somewhat scary security trade-offs.
Option B: Turnkey Service: Workspot offers a turnkey service for deploying your virtual desktops and workstations in the cloud. We do it for you, so in that sense, you don’t have as much control (although we work side-by-side throughout the deployment process) but your deployment is faster, easier to manage, and you’ll have predictable costs each month. Plus you have complete control to add desktops, remove desktops, and otherwise manage your entire implementation through a single management console. And though it’s counterintuitive, you will get stronger security than any other cloud desktop provider. And that’s where the secret sauce comes in, but more on that later!
Philosophical & Practical Differences Around Security
When comparing virtual desktop solutions, it’s important that you really drill down on the vendor’s approach to security. Workspot has a multi-pronged approach that no other vendor can approximate. The first aspect of security stems from our cloud-native architecture. Unlike other vendors, we developed our cloud virtual desktop solution from the ground-up. The Workspot Desktop Cloud architecture completely separates the configuration and provisioning control signals from the flow of data. Here’s what that looks like:
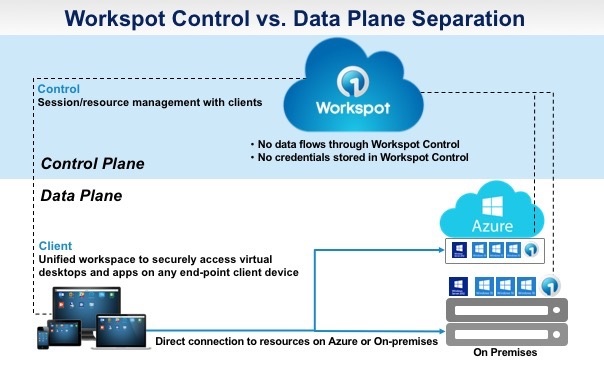
In a traditional VDI/DaaS solution, both data and control flow through the same paths – they are not separated as they are with Workspot. With these legacy solutions, the user has to connect to a broker to authenticate and the broker contacts a VM to provide the user with a virtual desktop. If the broker is managed by a 3rd party, that 3rd party can see all of the traffic flowing between the user and the virtual desktop. That is scary!
Workspot is different because of our architecture. When a user comes in from anywhere in the world from their laptop to connect to their virtual desktop, their data never traverses through the Workspot Cloud. Once the encrypted VMs are configured, users authenticate (via AD or MFA) and connect from any location (on-site or remote) to get a direct connection to their virtual desktops and resources; in other words, the client connects directly to the virtual Windows 10 desktop running in Azure, never through Workspot Control.
The second aspect of security is that we believe in the Principle of Least Privilege (PoLP). PoLP ensures the absolute minimum amount of access necessary to do the job. In this context, it’s about “access control”. Since there is no such thing as “fully secure”, what we can do is limit the plane of attack. See that tiny little white box on the left in the diagram below? That’s the plane of attack with Workspot. By following the PoLP and requiring the minimum access privileges to our customer’s corporate resources, Workspot has minimized the surface of attack to that tiny little white box while also providing the customer with full access to their AD, networking, firewalls, OS, VMs/Disk, data, and GPOs – along with the ability to control their own environment. In practice, this means that when we deploy your desktops in Microsoft Azure, we do it while having the absolute minimum admin access. This access is limited to configuring, deploying and managing the Windows 10 desktop VMs. Because we handle this for you, you get fast deployment (a few days, usually) and reliability (we’re always monitoring & we boast 99.95% uptime). All this WITHOUT having any ability to even peek into your VMs.
Conversely, see that big white box on the right side of the diagram? That’s all the other VDI/DaaS vendors; they can access your entire environment – the OS, disk, files, AD, data traffic. That’s a pretty big attack surface.
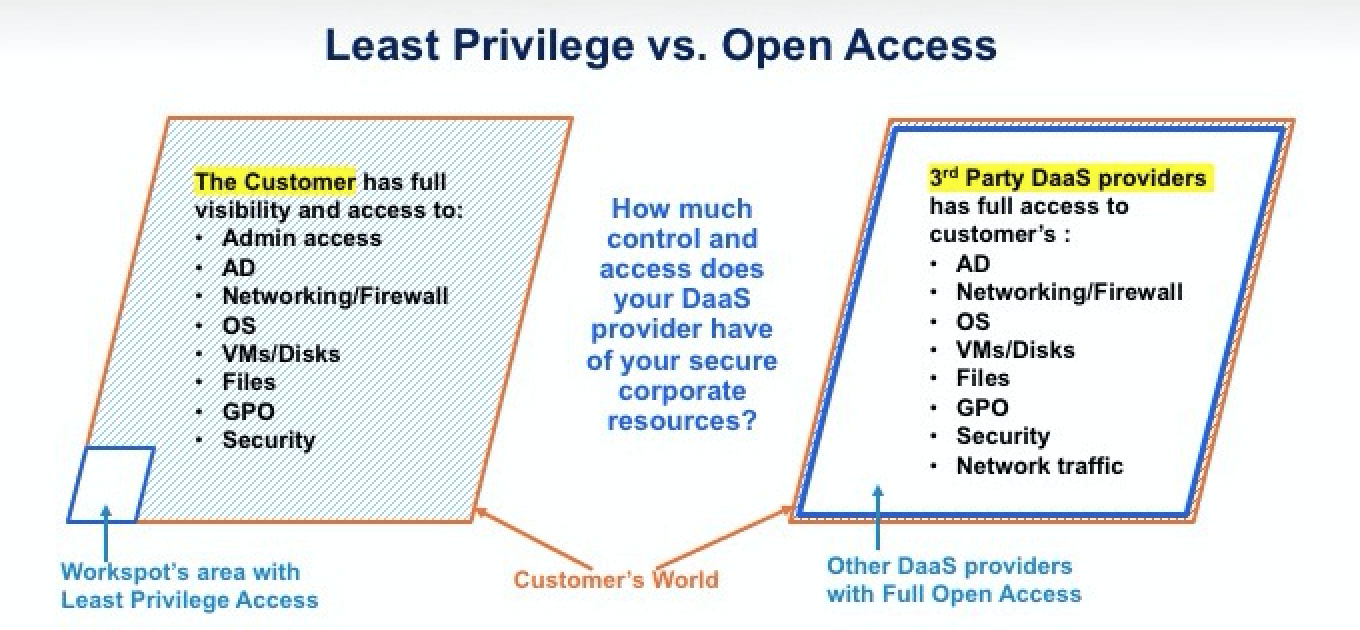
Workspot has no access to the customer’s corporate resources (left), whereas other VDi/DaaS providers have full visibility into these sensitive corporate resources.
When you talk to those other cloud VDI vendors, ask these important questions :
– How much access to my environment will you have?
– Where is my data?
The third aspect of security is top-secret! It’s our Secret Sauce. All you security experts reading this don’t expect us to reveal that in a blog do you? For that, we’ll need to talk!
Workspot Benefits
- Deploy in days, in any Azure region in the world!
- Robust enterprise security
- Better-than PC performance
- Flat rate subscription pricing
- 99.95% Desktop Cloud uptime and availability
With Workspot Desktop Cloud on Azure, your IT team retains full control of all corporate assets and has the ability to define granular user access controls according to the use case.
Now, how about some secret sauce? Schedule a live demo and we’ll show you how it works!